1. Information Technology (IT) Audit | |
 |
An Information Technology (IT) audit, or Information Systems (IS) audit, is an examination of the management controls within an Information technology (IT) infrastructure. The evaluation of obtained evidence determines if the information systems are safeguarding assets, maintaining data integrity, and operating effectively to achieve the organization's goals or objectives. Read More |
2. Vulnerability Assessment and Penetration Testing | |
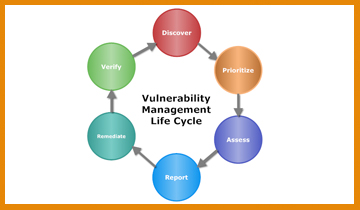 |
A Vulnerability Assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Examples of systems for which vulnerability assessments are performed include, but are not limited to, information technology systems, energy supply systems, water supply systems, transportation systems, and communication systems. Read More |
3. Cyber Crime Investigations | |
 |
Cyber Crime is defined as a crime in which a computer is the object of the crime (hacking, phishing, spamming) or is used as a tool to commit an offense (child pornography, hate crimes). Cyber - criminals may use computer technology to access personal information, business trade secrets, or use the internet for exploitive or malicious purposes. Read More |
4. Cyber Forensics | |
 |
In awareness activities, the learner is the recipient of information, whereas the learner in a training environment has a more active role. Awareness relies on reaching broad audiences with attractive packaging techniques. Training is more formal, having a goal of building knowledge and skills to facilitate the job performance. Read More |